
As soon as we talk about ransomware, we have to draw a line between the things it used to be and what it is. Why? Because today ransomware isn’t nearly encrypting data — it’s mostly about data exfiltration. Then, it’s data encryption and departing persuasive evidence that the attacker had been in the system, and finallyit’s extortion. And it’s not only about the data loss itself about publishing stolen info on the internet. Let’s phone it “Ransomware 2.0”.
Why is it important to state this? Because many organizations still feel that it’s about malware, also in case your anti-malware protection is good enough, you now ’ll be OK. As long as people believe that this way, the ransomware hazard actors will continue to triumph over and over.
In most cases, the initial vector of attack is harnessing some known vulnerabilities in commercial VPN applications. Other instances require abusing RDP-enabled machines subjected to the web. Then there’s the exploitation of the router firmware. As you can see, it’s not always about malware but also bad practices, too little patching cycles, and general safety procedures.
Occasionally ransomware threat actors can rely on conventional malware like botnet implants formerly dropped by other cybercriminal groups. And lastly, if we remember the Tesla story, the attempt to sabotage that factory was through somebody working in the provider. That means physical human access is also a vector. It is complex.
In all circumstances, the first entry point is to begin community reconnaissance, subsequently lateral movement, then data exfiltration. After it is done, it eventually comes into the “coup de grace” – that the ransomware. By the time ransomware is set up, the anti virus product may be deleted or disabled from the threat actor since they had complete control over the domain and could function as valid administrators. So it is about a whole red team operation that relies on various hacking techniques, such as those to disable anti virus solutions mostly through valid applications and misc scripts. In this way the threat celebrity doesn’t irritate if the ransomware itself will probably be discovered or not.
Different ransomware groups use various TTPs and different encryption techniques. Now we want to talk about two of these: Ragnar Locker and Egregor — a seasoned and a newbie. Both singular and distant at the identical moment.
Ragnar Locker
Early variations of this malware were found in 2019; nonetheless, Ragnar Locker gained notoriety at the first half 2020 as it started to attack massive organizations.
Ragnar Locker is highly concentrated, to the extent that every individual sample is specifically tailored to the company the actors are attacking. The group behind it loves to abuse RDP, although their preferred payment method is bitcoins.
This group owns three .onion domains accessible on Tor and one Surface Web domain listed on June 16, 2020.
If the sufferers refuse to pay, their stolen data is printed in a so-called Wall of Shame section.
Screenshot of the Wall of Shame where stolen data is exposed
Curiously, this group is positioning itself as a insect hunting group. They assert the payment is the bounty for detecting vulnerabilities that were exploited and also to provide decryption for the documents and OpSec training for your sufferer; also, ultimately, just for not publishing the stolen data. Needless to say, if the victim will not pay, the data goes public. Besides that, in the event the sufferer chats with the Ragnar Locker hazard celebrity and fails to pay, then the conversation is exposed along with the stolen data.
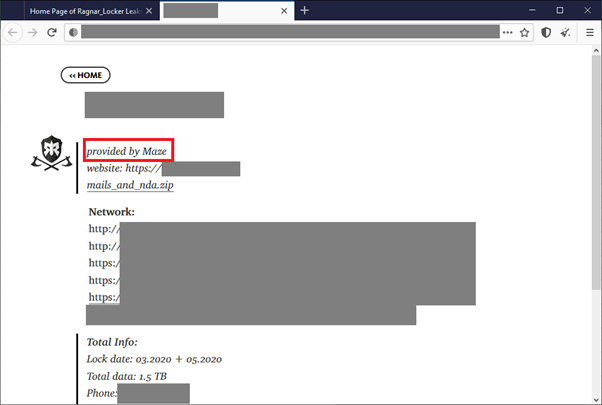
Back in July 2020, Ragnar Locker made a public announcement they had joined so-called “Maze Cartel” distraction concept. This means to state that the groups whined, exchanging data stolen from sufferers and publishing it on their websites.
Instance of a sufferer allegedly supplied by Maze and printed within the Ragnar Locker Wall of Shame webpage
You can read more about Maze Ransomware here.
Depending on the record of victims who refused to pay, the most important goal of Ragnar Locker are US based firms, although the type of industry varies.
! Function(e,I,n,s)var t=”InfogramEmbeds”,p =e.getElementsByTagName(“script”)[0];if(window[t]&&window[t].initialized)window[t].process&window[t].process();else if(! E.getElementById(n))var o=e.createElement(“script”);o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(record,0,”infogram-async”);
Geography of Ragnar Locker sufferers (download)
! Function(e,I,n,s)var t=”InfogramEmbeds”,p =e.getElementsByTagName(“script”)[0];if(window[t]&&window[t].initialized)window[t].process&window[t].process();else if(! E.getElementById(n))var o=e.createElement(“script”);o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(record,0,”infogram-async”);
Ragnar Locker sufferers by industry (download)
Technical description
For our investigation we decided a newly encountered sample of the malware: 1195d0d18be9362fb8dd9e1738404c9d
When started, Ragnar Locker assesses the system locale of the system it is executing on. If determines that it is the locale of one of the states listed in the screenshot below, it is going to stop operation and exit without doing anything .
For states not on the above record, it will proceed to prevent services with names containing any of the substrings hardcoded from the malware sample along with obfuscated from RC4:
Later, Rangar Locker will terminate running processes based on a Different substring list contained within the Trojan body:
Ultimately, when all of the groundwork is done, the Trojan will look for accessible drives and encrypt the victim’s documents.
For record encryption RagnarLocker employs a custom stream cipher based on the Salsa20 cipher. Instead of the normal initialization ‘magic’ constants sigma = “expand 32-byte k” along with tau = “expand 16-byte k” normally utilised at Salsa20, the Trojan generates new random values for each file that is processed. This is an unnecessary measure which makes the cipher harmonious with the typical Salsa20, but doesn’t in reality enhance its safety.
The primary and nonce values are also uniquely generated for each record, which is encoded in addition to the constants described previously by RSA using the public 2048-bit key hardcoded from the Trojan’s body.
The RNG is based upon the MS CryptoAPI function CryptGenRandom, which is deemed secure, as well as also the SHA-256 hash algorithm. The RNG implementation seems somewhat awkward, however we haven’t found any vital flaws inside.
The RNG procedure pseudocode Employed by a New Ragnar Locker variant
After encrypting the content of each one of the victim’s documents, Ragnar Locker will append the encoded key, nonce and initialization constants into the encoded file, and then finalize by adding the marker “! @#_®agna®_#@! ”
Trailing bytes of a file encoded by Ragnar Locker
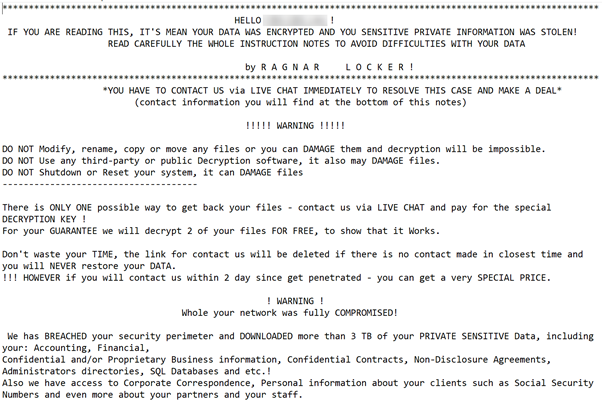
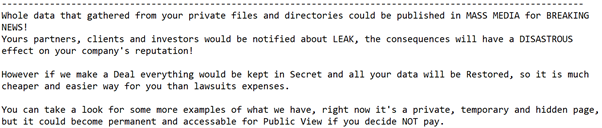
The ransom notes fell from the Trojan include the name of the sufferer organization which clearly indicates that the criminals utilize a concentrated approach, identify their victim and carefully prepare the attack.
The ransom note additionally attempts to additional scare the sufferer to paying by highlighting that the threat actors have stolen confidential data in addition to the file encryption done by the Trojan.
Egregor
Egregor ransomware is a new breed that was discovered at September 2020, and after the initial analysis we noticed signal similarities between this newest hazard and Sekhmet ransomware, as well as the infamous Maze ransomware, which declared November 1st, 2020 they shut down.
Egregor keeps a minumum of one .onion domain name and two Surface Web domains. The very first Surface Web domain name was registered on September 6, 2020 and also the next one on October 19, 2020. In the time of writing, both Surface Web domains were intermittent. That is probably why on the Primary page of the Onion domainname, There’s a large disclaimer for this notice:
The Egregor ransomware is typically distributed by the criminals after a community breach. The malware sample is a DLL file that needs to be found with the proper password given as a command line argument. The DLL is generally dropped by the Internet. On occasions, the domains used to spread it exploit words or names used from the victim’s industry.
Egregor is probably the most aggressive Ransomware family in terms of negotiation with the victims. It provides just 72 hours to get in touch with the threat celebrity. Otherwise, the victim’s info is processed for publishing.
The ransomware payment has been negotiated and agreed upon through a particular chat assigned to every victim. The payment is received in BTC.
Instance of a conversation negotiating to pay the ransom
Technical description
b21930306869a3cdb85ca0d073a738c5
As mentioned previously, the malware sample only works if a right password is provided through launch. The packer of the malware may use this password to decrypt the payload binary. A missing or incorrect argument is going to lead to an incorrect decryption of the payload, which may be not able to perform and will crash rather.
This technique is intended to hinder both automatic investigation in sandbox-type systems, and guide analysis by investigators: without the correct password it is not possible to unpack and examine the payload binary.
After unpacking two layers of the malicious packer, we wind up with an obfuscated binary which is still not acceptable for static analysis. The obfuscation techniques used in Egregor strongly resemble those at Maze and Sekhmet: that the code will be ‘torn apart’ by control flow obfuscation utilizing conditional and unconditional jumps, PUSH+JMP instead of RETN, and so on.
Control flow obfuscation illustration
After the payload begins executing, Firstly, it will check the machine and user terminology of this OS to avoid encrypting machines having one of the following languages installed:
Armenian (Armenia)
Azerbaijani (Cyrillic, Azerbaijan)
Azerbaijani (Latin, Azerbaijan)
Belarusian (Belarus)
Georgian (Georgia)
Kazakh (Kazakhstan)
Kyrgyz (Kyrgyzstan)
Romanian (Moldova)
Russian (Moldova)
Russian (Russia)
Tajik (Cyrillic, Tajikistan)
Tatar (Russia)
Turkmen (Turkmenistan)
Ukrainian (Ukraine)
Uzbek (Latin, Uzbekistan)
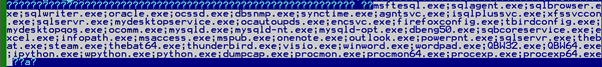
Then it will Try to terminate the following processes:
This is intended to make writable potentially invaluable documents such as databases or documents that may have been in use in the moment of disease. Moreover, some programs typically employed by investigators, e.g., procmon or even dumpcap, are also listed for termination to hinder dynamic investigation.
Egregor uses a hybrid file encryption scheme based on the flow cipher ChaCha and the asymmetric cipher RSA.
Even the RSA-2048 master public key of these criminals is embedded in the trojan’s body.
When executing on a victim’s device, Egregor generates a new special set of session RSA secrets. The session private RSA key is exported and encrypted by ChaCha using a distinctively generated key + nonce, and then the primary and nonce are encoded from the master public RSA key. The results are saved in a binary file (in our case it’so-called C:\ProgramData\dtb.dat), as well as a base64-encoded string from the ransom notes.
For every data file Egregor processes, it generates a fresh 256-bit ChaCha key and 64-bit nonce, encrypts the file content from ChaCha, then deletes them using the session public RSA key, and saves them along with some additional data in the end of the encrypted file.
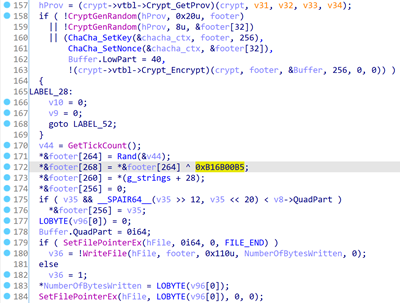
The last 16 bytes of every encrypted file are comprised of a dynamic marker: a random DWORD and also this identical DWORD xor’ed with the significance 0xB16B00B5 which equals ‘BIGBOOBS’ in so-called leet speak, initially employed by “hackers, crackers and script kiddies”, according to Wikipedia.
Part of the file encryption procedure pseudocode
The main page of the data flow site contains information about recently attacked companies along with some humorous comments composed by the ransomware group.
The record section of the site lists the sufferers of the extortionists and also the links to download the stolen data.
Depending on the information of those sufferers who refused to pay, the geographic reach of Egregor is far more extensive than that of Ragnar Locker:
! Function(e,I,n,s)var t=”InfogramEmbeds”,p =e.getElementsByTagName(“script”)[0];if(window[t]&&window[t].initialized)window[t].process&window[t].process();else if(! E.getElementById(n))var o=e.createElement(“script”);o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(record,0,”infogram-async”);
Geography of Egregor sufferers (download)
The Exact Same goes for the number of attacked businesses:
! Function(e,I,n,s)var t=”InfogramEmbeds”,p =e.getElementsByTagName(“script”)[0];if(window[t]&&window[t].initialized)window[t].process&window[t].process();else if(! E.getElementById(n))var o=e.createElement(“script”);o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(record,0,”infogram-async”);
Egregor sufferers by industry (download)
Conclusions
Unfortunately, Ransomware 2.0 is here to remain. As soon as we talk about 2.0we suggest concentrated ransomware with data exfiltration. The entire extortion procedure is mainly about the victims’ data not being published on the internet and just then about decryption. Why is it important for the sufferers that their data isn’t published? Because possible suits and fines because of violations of legislation like HIPAA, PIC or even GDPR can lead to immense monetary losses, reputational damage and potential bankruptcy.
As long as companies see ransomware threat actors as malware threats, they may also fail. It isn’t about merely endpoint protection; it is about red teaming, business analysts working with exfiltrated documents assessing the ransom to pay. It is also about data theft, clearly, and public shaming, resulting in a variety of problems in the end.
The next chapter will cover something else — a perfect umbrella for distinct threat actors with unique motivations working under the aegis of all Ransomware 2.0.
Article Source and Credit securelist.com https://securelist.com/targeted-ransomware-encrypting-data/99255/ Buy Tickets for every event – Sports, Concerts, Festivals and more buytickets.com











Leave a Reply
You must be logged in to post a comment.